SecureAuth has introduced a new attack detection engine – Dynamic IP Blocking. The new technology is the latest security innovation from SecureAuth, further strengthening the first line of defense to protect authentication endpoints.
What is Dynamic IP Blocking?
Introduced in mid-2020, SecureAuth Dynamic IP Blocking temporarily blocks IP addresses used by bad actors to generate a password spraying attack against the platform. Like the principles used in a modern IDS/IPS Unified Threat Management system, Dynamic IP Blocking incorporates a proprietary pattern recognition algorithm to detect and mitigate attacks without user or admin intervention.
The Threat of Password Spraying Attacks
Password spraying is a low-speed and particularly dangerous password attack method often performed against single sign-on (SSO) and cloud-based authentication portals. You can think of password spraying as a reverse brute-force attack. Bad actors use a unique password against a myriad of user account names hoping to breach that single account.
In a brute-force password attack, the malicious hacker rapidly progresses through a combination of a single username paired with dozens of potential common passwords with the hope of compromising the account. In the password spraying attack, the hacker tries thousands of usernames with the same password before moving on to a second password.
The danger of the password spraying attack lies in the fact that the attack is slow against each individual username with long delays between each login attempt. Therefore, the hacker can avoid triggering the failed login attempt detection (also known as SecureAuth Password Throttling) and run the attack undetected.
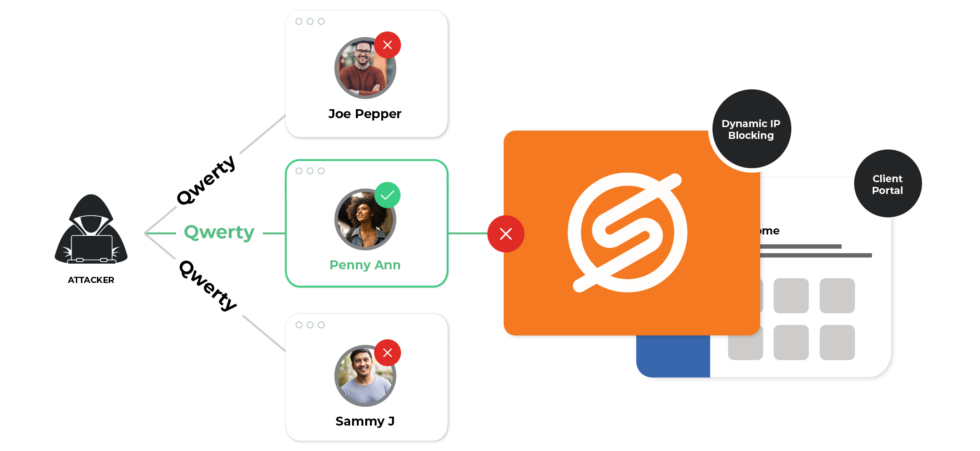
How Dynamic IP Blocking Protects Against Attacks
SecureAuth Dynamic IP Blocking technology prevents the originating IP address from submitting requests after a specified number of failed login attempts using different usernames within a specified period of time. Instead of locking user accounts, it blocks login attempts coming from the IP address.
It’s worth noting that Dynamic IP Blocking works for both legacy clients (installable software using WS-Trust) and modern clients such as web apps using SAML.
Configuring Dynamic IP Blocking
To use Dynamic IP Blocking, go to your SecureAuth Identity Platform Administration Console. First, set the length of time to block the IP address after a set number of failed attempts. Your setting will apply to login workflows in all policies. Then, you add the Dynamic IP Blocking rule in each policy.
Step-by-Step Configuration Guide
- Access IP Filtering Settings:
On the left side of the Identity Platform page, click IP Filtering. Note that the settings you define here apply to all policies.
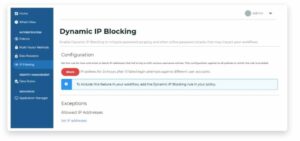
- Set Blocking Duration and Threshold:
Set the length of time to block associated IP addresses after a specified number of failed login attempts.
Options include:- Length of time – 12, 24, 36, 48, or 72 hours
- Number of failed login attempts – 5, 10, 15, 20, and 25
- Allow Specific IP Addresses:
To allow certain IP addresses, click Set IP addresses link and enter IP addresses, separated by a comma. Note: IP addresses can only be in IPv4 format.
- Apply Blocking Rules to Policies:
Next, open a policy and go to the Blocking Rules tab and add Dynamic IP Blocking as a new rule.
Availability and Next Steps
Dynamic IP Blocking is included in select SecureAuth SaaS subscription plans. Contact us and schedule a demo to learn more about how Dynamic IP Blocking can enhance your security posture and protect against advanced threats.
Why Choose SecureAuth?
SecureAuth’s innovative approach to Dynamic IP Blocking sets it apart from other IAM providers. By incorporating a proprietary pattern recognition algorithm and providing seamless integration with both legacy and modern clients, SecureAuth ensures that your organization is protected against the most sophisticated password spraying attacks.
